The European Space Agency hopes to send into orbit later this year a satellite that will let its partners explore the potential of using quantum mechanics to secure long-distance communication. But it is far from the first to try. Eagle-1 will join China’s Micius, which has been in orbit for almost eight years as part of the country’s Quantum Experiments at Space Scale (QUESS) experiment, and another much smaller probe launched in 2022.
It is close to six decades since the idea first appeared, though it lingered in obscurity and unpublished until the early 1980s. At the December 1983 International Conference on Computer Systems and Signal Processing in Bangalore, Charles Bennett of IBM Research and University of Montreal professor Gilles Brassard reinvigorated the idea.
The pair proposed a protocol built around the Heisenberg uncertainty principle. This sets out that measuring one aspect of a quantum state makes it impossible to determine other properties of the same particle that went into creating the quantum state before the measurement took place.
One way to encode bits in quantum states is to use polarisation. A zero may be transmitted as light polarised at 0° and the one as a photon polarised to 90°. The Bennett-Brassard 1984 (BB84) protocol extends this by offering a second pair of angles, at 45° and 135°. The sender flips randomly between these two bases to camouflage the data.
Thanks to Heisenberg’s principle, a receiver has only one chance to get the decision right on how to set the angle of a polariser to detect the data correctly. Given a string of bits where the polarisation basis is selected randomly, there is a 50% probability of each photon being aligned correctly with a receiving polariser.
Under the protocol, the intended receiver is in contact with the sender using a conventional communications channel and they use this to confirm whether they received the bits sent correctly. Because of the destructive nature of quantum measurement, if an interloper has attempted to read the data and regenerate it with new quantum states before despatching to the intended recipient, the sender will see discrepancies. As long as there are no physical weaknesses in the equipment used for transmission and reception, the users can perform the check without disclosing bits in the key they agree between themselves.
The QUESS experiment, among others, uses entanglement rather than polarisation for the quantum channel. Here, the sender and receiver measure a state from each half of a pair of entangled photons. The sender’s manipulation of the quantum state affects what the receiver will see when they finally measure it.
Researchers have come up with various improvements on BB84. Many have focused on an improvement known as the decoy-state protocol. This uses different photon intensities to convey the data. The two parties share bit-error rate data as well to help them home in on eavesdroppers.
Though the technology remains largely experimental, organisations have applied BB84 and its variants. In 2007, the Swiss government used it to protect data used in the country’s elections. Banks have been among the earliest commercial adopters. They see quantum technology as a way to better secure the backup of secure data transmitted between their data centres.
The issue of speed
One issue with BB84 is speed. Data exchange is a slow process using any of these protocols, on the order of megabits per second rather than the multi-gigabit rates of classical channels. Instead of trying to secure bulk data, the typical aim of these quantum systems is to strengthen the weakest link when it comes to encryption: securing the keys themselves.
Symmetric encryption is often the choice for sending bulk data but it lacks the inherent key security of asymmetric techniques such as elliptic-curve encryption: you have to send the full decryption key to any intended recipients. Quantum channels armed with the right protocols provide a much higher guarantee of security than even longstanding key-exchange protocols such as Diffie-Hellman. Though comparatively slow, quantum key distribution (QKD) is fast enough to let users change shared-key values frequently.
There are, however, snags. In the 2007 Swiss elections, the transmissions only needed to travel around 50 miles per hop. The need to regenerate signals using amplifiers in fibre-optic networks runs afoul of the no-cloning issue. You cannot simply copy the state and send the new photon on its way without the repeater being treated as an eavesdropper. At least, not yet.
China’s completion of a $85m fibre-optic network running 1,200 miles from Beijing to Shanghai seemed to fly in the face of such distance limitations when the record for a single QKD exchange was 102km set in 2015. Exchanges through this link relied on stations at each hop getting the key in a BB84-type exchange and then starting another session to send the key to the next station down the line. The long-distance link needs more than 30 trusted nodes.
Space, on the other hand, is a lot more forgiving. China’s QUESS experiment showed that photons travelling through free space suffer lower losses, though passing the key bits back to Earth can only happen when the satellite is quite close to a ground station. This setup made it possible to use a quantum channel to send video almost 5000 miles from China to the Institute for Quantum Optics and Quantum Information in Vienna.
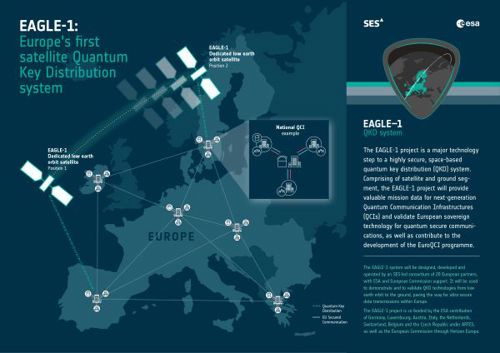
As with fibre-optic networks on the ground, satellite QKD has vulnerabilities. The free-space links are vulnerable to jamming. Though scientists at Padua University demonstrated a link that can operate in strong sunlight over a distance of 150m, Micius mostly operates at night because of the effects of background light. And, though it is notionally harder to hack an orbiting satellite than a ground station to retrieve the key bits when they are decoded before being relayed to the next station, this is far from guaranteed.
Improvements to the reliability of the equipment used to prepare entangled pairs of particles and to detect may make it possible to implement a workaround for the no-cloning principle. Experiments have shown quantum repeaters are potentially viable. These devices swap entangled states between pairs of photons that were created on separate links. By performing multiple swapping procedures, repeaters extend an entanglement across the entire length of the network. The process reduces data rates because not every operation will be successful. But the penalty may still work out a lot lower than trying to extend the reach of individual fibre links.
Though generating single photons or entangled pairs of them and detecting them remains tricky to do, attempts to integrate the necessary components into small packages have progressed relatively quickly. Parallel research into photonic quantum computers has helped here. For detection, avalanche devices based on indium phosphide seem to offer the best prospects. And silicon provides most of the tools needed for manipulating photons, which makes system-in-package implementations highly feasible.
In 2021, Toshiba showed the results of a project part fund by the UK’s Industrial Strategy Challenge Fund. The company built a hardware random number generator and transmitter and receiver components for a QKD system that were into the standard pluggable modules used for conventional fibre-optic links. FPGAs in the packages control the production of phase-encoded photons by indium phosphide-based lasers. Silicon waveguides provide the ability to modulate and steer the pulses electrically.
While organisation such as the ESA attempt to catch up, Chinese scientists are hoping to build a global space network for QKD using up to eight satellites in a mix of low and medium-Earth orbits. As integration and understanding of quantum effects improve, it probably won’t take another 40 years for QKD to become the foundation for many security systems. Unlike Diffie-Hellman, it is if implemented properly guaranteed quantum-safe.
Image: Toshiba built a hardware random number generator and transmitter and receiver components for a QKD system used for conventional fibre-optic links.













