There are two main types of hardware attack. One is to try to subvert the device in normal operation, generally by attaching something to an I/O port or to the PCB itself. This is the world that games players may know through "modchips".
"Back in the day if you wanted to play ’backup copies’ of your games, you’d solder some wires into your game console," SecuringHardware researcher Joe Fitzpatrick explained at the Security Analyst Summit in spring 2018.
The extra wires and, sometimes additional ICs, would defeat the copy protection mechanisms manufacturers built into their consoles.
Counterfeiting has also become a way of employing modchips. Fitzpatrick pointed to a post on Reddit from a couple of years ago in which a user opened up some network switches carrying the Cisco brand that were bought on Reddit that looked to be sporting a modchip. The modification turned out to be a patch to fix a problem on the core PCB that allowed faulty parts to operate more or less correctly.
Such counterfeiting attempts have led chipmakers to explore the use of encryption inside a system to check whether peripherals are legitimate or have been exchanged for fakes. Initially developed for inkjet cartridges – which has a sizeable aftermarket for refilling and fakes – STMicroelectronics, for example, has the STSafe line of devices. These devices have found applications that range from gaming to medicine.
Another level of attack is to try to peer more deeply into the target in the hope of reverse-engineering the design or to pull out encryption keys and other sensitive data that should, according to the data sheet, never be recoverable once a fuse is blown or a write-only bit set. The clock signals and power rails are the main targets. A clock attack tends to consist of stopping the clock in mid-cycle or adding glitches to create ultrashort clock cycles. When it comes to power, the favoured trick is dropping the supply voltage, which prevents all or some of the active transistors from switching properly. In all these cases, logic paths start to fail. Timing is critical for these attacks, which can mean altering the power supply to take out decoupling capacitors that can smooth out the changes in power.
If hit at the right time, a processor may execute instructions incorrectly or simply run the wrong instructions. A type of attack that researchers at security consultant Riscure found worked on an older Arm processor architecture was to force the core into a privileged mode that opened up a range of software hacks. Aberrant bus activity can corrupt processor registers, I/O registers or memory that help cut the time needed to perform side-channel analysis (see "Careless whispers", January 2018).
Some of the physical attacks are ingenious although they may turn out to have a short shelf life. Last year, Connor Bolton and colleagues from the University of Michigan and Zhejiang University found it is possible to attack hard disk controllers through the vibration sensors that are meant to protect them. Low-frequency audio with strong resonant frequencies could cause sudden movement in the read head, potentially damaging data or reducing read and write bandwidth to the point where system software times out and is forced to reset.
There are ways to protect against these attacks. An onchip clock source makes it much harder for a hacker to use that kind of attack – their only option is to decap the chip and try to find the onchip generator. A second level of protection is often a metal shield over the most sensitive circuitry. If this is broken, the device simply refuses to start up.
Historically, the built-in reaction to glitch hacks has been as blunt as some of the attacks themselves. This is often seen with power attacks. Brownouts are tougher for any chip to deal because they stop protection circuitry in its tracks as well as the hacker’s target. But watchdog circuits can at least monitor the power rails and just reset the chip if it suspects corruption has occurred, forcing the hacker to start their attack again once the device has rebooted. With too many brownouts, it may go further.
"The chip architect is supposed to design the system such that it reacts to the indications from the processor and responds accordingly. For example, if the parity check fails then it could be that the the chip erases memory and resets," says Asaf Shen, vice president of security marketing at Arm.
Continual resets can do a lot to slow the hacker down and maybe look for a softer target. But when dealing with attacks focused on taking over a larger system, the reaction can be as effective in enabling a denial-of-service attack. An alternative may be to use checkpoints and traps similar to those used to deal with memory errors. Whenever the system detects a glitch that looks likely to be deliberate, it invokes a trap handler that rolls back to the last known saved state. Work by Bilgiday Yuce at the Virginia Tech has followed this approach to build glitch-tolerant processor circuitry. At some point, the load may be too much. System software can analyse the pattern of events and then decide whether it is better to continue or invoke an orderly shutdown.
Although the manufacturers of microcontrollers have put protection against glitching attacks into their devices, they have typically restricted these mechanisms to the devices that present the juiciest targets for hackers. But that could change.
"As far as glitch attacks are concerned, the original targets were definitely payment oriented designs, because it is pretty obvious that those equipments provide the highest incentive for hackers to develop innovative strategies. As always with new kind of attacks, if proven successful they then develop and grow into more cost effective, more common threats," says Gregory Guez, executive director of embedded security at Maxim Integrated.
IoT device manufacturers may find themselves having to deal with both counterfeit detection – by only enabling I/O devices that successfully respond to a challenge-response protocol or supply a valid code number – as well as glitch attacks. The key question is how much of a target a non-payment system is likely to be.
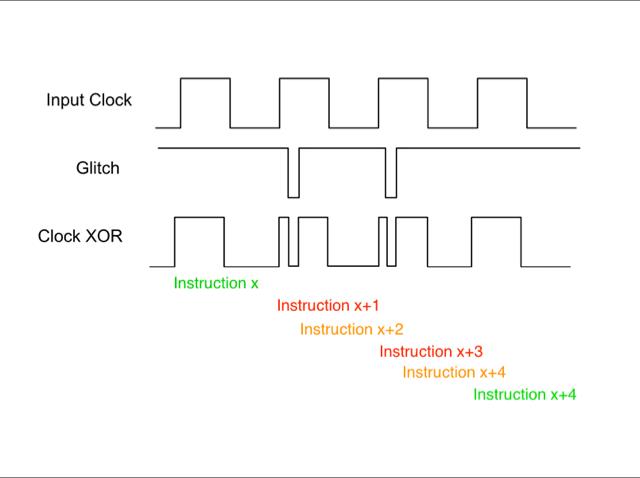 Above: Diagram illustrating how glitches can invoke a clock attack on a processor
Above: Diagram illustrating how glitches can invoke a clock attack on a processor
Penetrating an individual IoT device may not deliver much of a financial reward on its own, but if a low-end controller is subverted by a hacker it can support a far more damaging attack. Although apparently compromised by a network rather than a physical attack, a fish-tank’s temperature-control system provided the way into a casino’s core network – ultimately leading to servers being robbed of sensitive data. Privilege-escalation hardware attacks could be instrumental in similar hacks, leading designers to use on-chip sensors in a wider range of devices.
Arm’s Cortex M-35P was designed to come with a portfolio of options intended to fend off typical invasive and non-invasive attacks because as Shen points out:"Physical attacks are getting easier and cheaper."
The tamper protection is on top of the existing M-series’ Trustzone software-isolation scheme and include support for parity checks on internal buses to detect the consequences of induced faults. "There are many different internal checks built into the operation of the [Cortex M-35P] that either prevent or report an invasive attack," Shen says.
Some designers may choose to roll their own checking circuitry into ASICs and SoCs. Ramsay Allen, vice president of marketing at Moortec, which has developed a range of on-chip temperature, process and voltage sensor IP cores says the company has started to see interest from customers in using the power monitors to check for potentially malicious brownouts. In the meantime, manufacturers need to be on the lookout for the fast-changing landscape of hardware hacking – and avoid becoming the next victim in the hunt for a jackpot.













