Despite these advances, vehicle advanced driver assistance systems (ADAS) are still operating as standalone systems. Each vehicle acts as an island among islands, executing a continuous loop of observe and react similar to human drivers, only faster. However, we can’t react to what we don’t see – and the same is true for even the highest resolution cameras. Dedicated short range communication and 5G wireless communication is changing this forever.
Vehicle-to-anything (V2X) communication is the next generation of connected car capability, allowing for real-time communication between vehicles, road-side equipment, traffic management centres and smart devices. The technology is being heavily promoted by the US Department of Transportation (USDOT) through issuance of a new proposed rule mandate last year and continued funding of proof of concept prototypes, now evolving into connected vehicle pilot programmes across Florida, New York and Wyoming. The reasoning behind the support dates back to decades of research. A 2011 study concluded that ‘deployment of connected vehicle systems and the combined use of vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) applications have the potential to address 81% of unimpaired driver crashes in all vehicle types’. Put into context, of the 32,885 traffic deaths that year, more than 26,500 accidents could have been prevented and lives saved.
Starting with the 2017 Cadillac, V2X-enabled vehicles will be able to send and receive basic safety messages through a wireless radio link. Received messages are combined with current ADAS inputs to extend visibility beyond sight lines to substantially prevent accidents. Several basic safety messages are broadcast per second in moving vehicles, including speed, GPS, position, size and brake status. These messages are received by vehicles within a 300m range and used to determine necessary alerts and actions. With V2V applications like left turn assist and emergency electronic brake light, accidents and pile ups due to fog and weather will be a thing of the past.
USDOT understands the success of V2X technology depends on cybersecurity and integrity of the safety messages. For V2X to be successful, the system must be designed so hackers are prohibited from modifying messages in transit and sending false messages as a valid end entity (EE). An EE is any system, vehicle or roadside equipment communicating on the network. For this reason, USDOT has partnered with Crash Avoidance Metrics Partners (CAMP), a consortium of seven major automotive manufacturers, to develop the security specifications and proof of concept prototypes behind V2X. The research performed by CAMP and its security industry partners are setting the groundwork for the deployment of the largest public key infrastructure (PKI) in history, once the new proposed rule making policy (NHTSA-2016-0126) goes into effect.
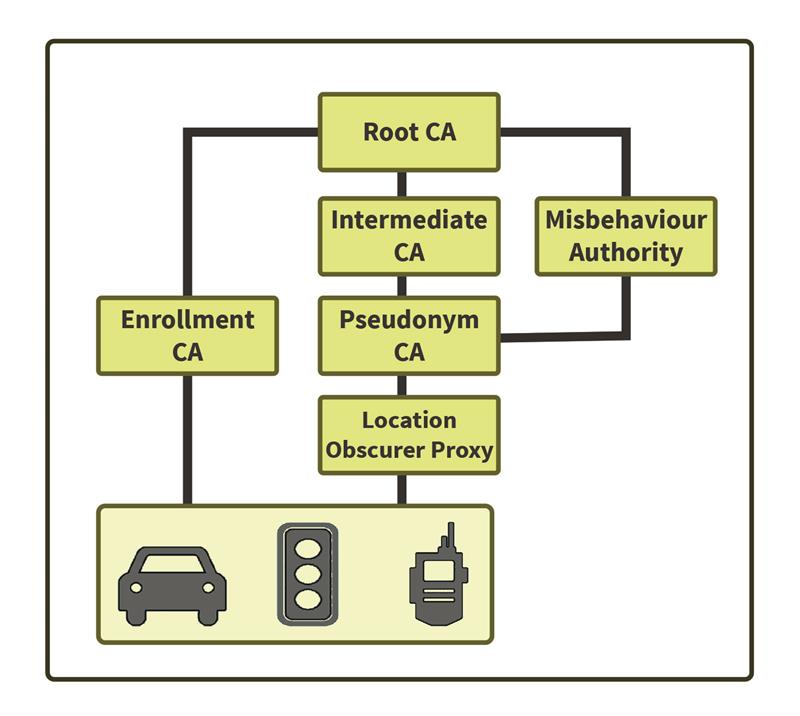 SCMS uses the latest PKI security to protect V2X messages and driver privacy
SCMS uses the latest PKI security to protect V2X messages and driver privacy
CAMP and industry partners continue to refine the IEEE1609.2 protocol stack and Security Credential Management System (SCMS) to protect safety messages and driver privacy. IEEE 1609.2 operates on EE devices, much like any network stack, to send and receive messages over any wireless link. Implicit certificates are used in the protocol to reduce size and keep EE devices from having to know each other beforehand. All outgoing safety messages are digitally signed, while incoming messages are verified to ensure they can be trusted.
V2X security uses digital signatures, per IEEE 1609.2-2016, to preserve the integrity of basic safety messages. Since vehicles and roadside equipment need to trust each other, a certificate is included with each message containing a public key corresponding to the private key used to sign the data. When messages are received, the EE first verifies the certificate before using the enclosed public key to check the data. As with all PKIs, the certificate is trusted because it was created and signed by a certificate authority (CA).
The V2X certificate authority consists of sub CA systems, each authorised to generate certificates, under a common root. The CAMP SCMS Proof of Concept Implementation Project provides security services for federally funded V2V and V2I connected vehicle pilot programmes through 2020. The purpose is for research and development only, with the goal of ‘extracting policies, procedures and lessons learned from the design, deployment and operations with a focus on generating public documents for stakeholders who are interested in establishing a National SCMS’.
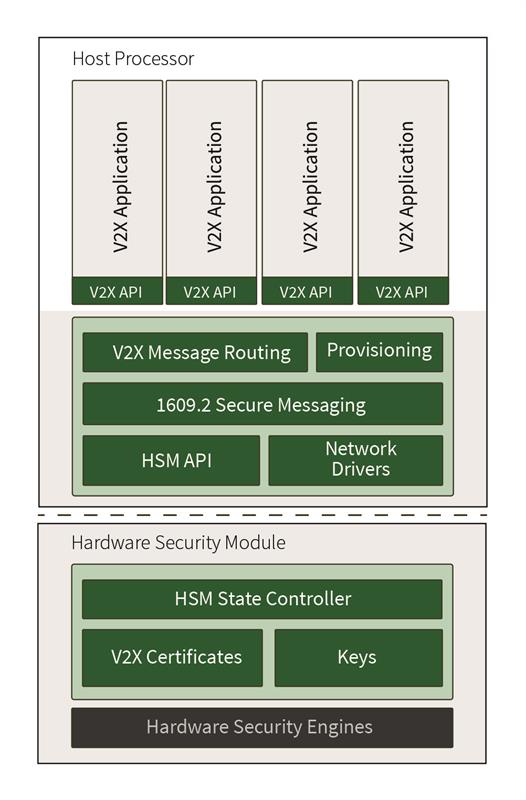 End entities must protect private keys and operate reliably using best practice security architectures
End entities must protect private keys and operate reliably using best practice security architectures
For commercial development, the INTEGRITY Security Services (ISS) Certificate Management Service (CMS) offers test and production certificates for all OEMs and suppliers preparing for the Notice of Proposed Rulemaking mandate. The ISS CMS distributes V2V and V2I certificates securely direct to vehicle and roadside communication devices. The ISS CMS supports both secure distribution of certificates in manufacturing and over-the-air top-off refills.
In order to ensure interoperability and security of end entity V2X devices, the industry is looking towards the OmniAir Consortium to develop technical specifications. OmniAir has more than 40 participating members and is assuming a leadership role in interoperability testing by organising the next ‘Plugfest by the Bay’, which takes place in San Francisco from 16 to 20 October. Vendors from around the world are coming together to verify interoperability, prior to engaging in OmniAir’s certification process. The previous event in May saw more than 200 attendees from 35 companies and 17 different countries. With test certificates provided by the ISS CMS, vendors are able to verify the CAMP specified EE-to-SCMS message protocol and responses including Enrolment Certificate Signing and Pseudonym Certificate requests.
Kerckoffs’ principle states that a crypto system should be secure, even if everything about the system, except the key, is public knowledge. The same is true for V2X. While interoperability testing continues, industry has begun discussing how production keys should be protected within an EE. Power on self-tests, secure boot, separation and secure updates are recommended to protect the reliability of the EE and V2X signing keys. Along with certification according to the US Federal Information Processing Standard, the merit of each security feature is being evaluated to determine the best solution. “Independent, third party certification for interoperable devices is a vital step that reveals a level of readiness and maturity of the technology,” said OmniAir’s executive director Jason Conley. “Security certificate authorities are also looking at third party certification to meet standards defined by USDOT and OmniAir before granting production certificates.”
V2X technology is about to improve vehicle safety substantially – made possible by years of research engineering a new real-time wireless network where security is built-in from the ground up. Certification ensures proper implementation of standards and should be necessary prior to receiving credentials, all leading to the ultimate goal of V2X technology, to produce messages we can trust. With security addressed, application developers are free to innovate new ways to share critical information and further save lives.
Author profile: Gregory Rudy is director of business development with INTEGRITY Security Services (a Green Hills Software company).













